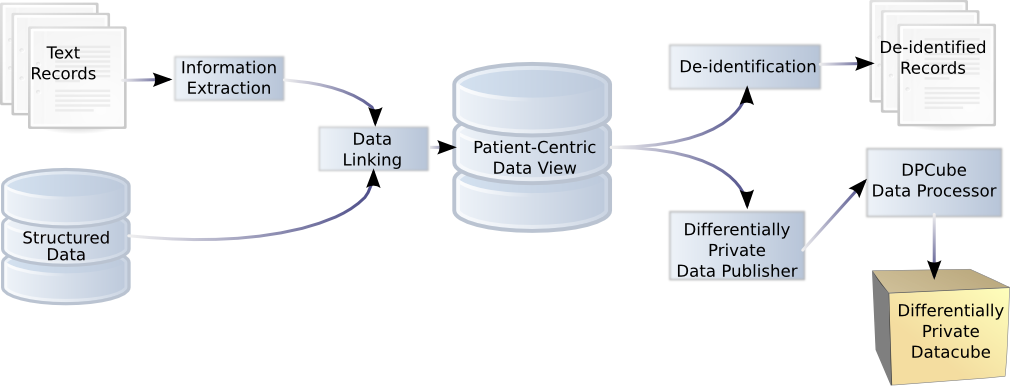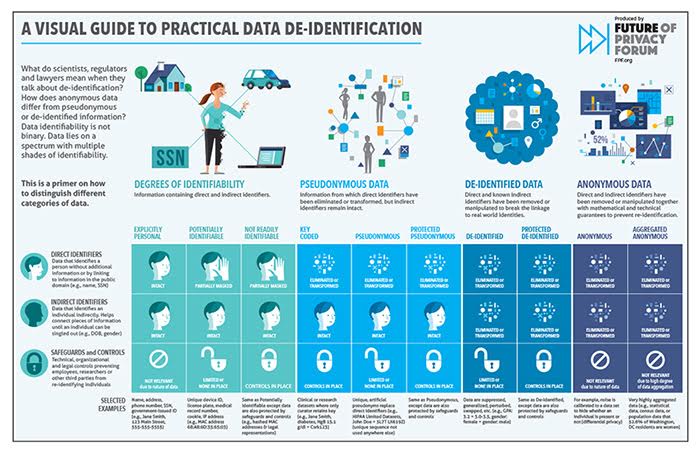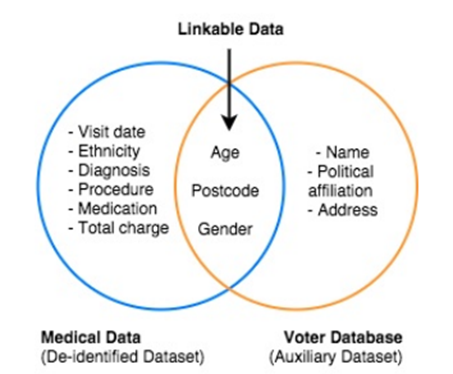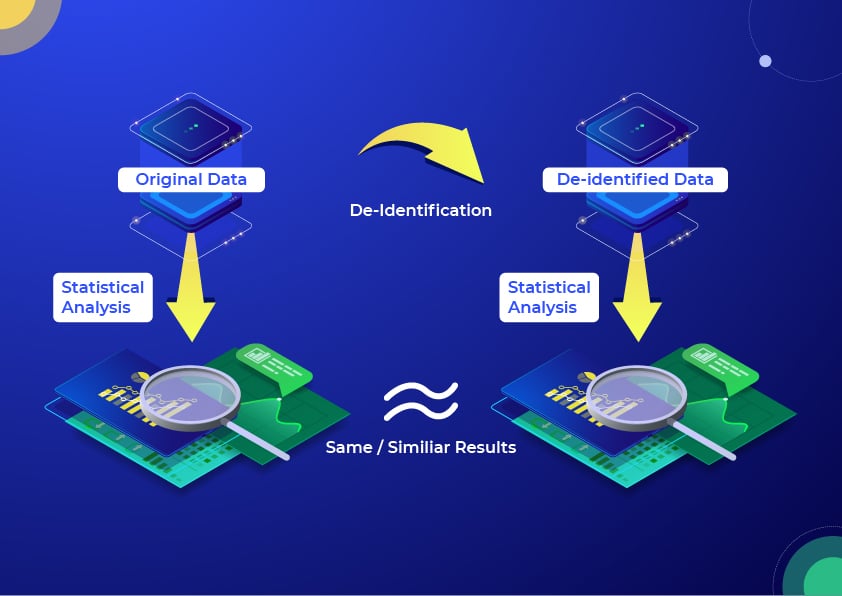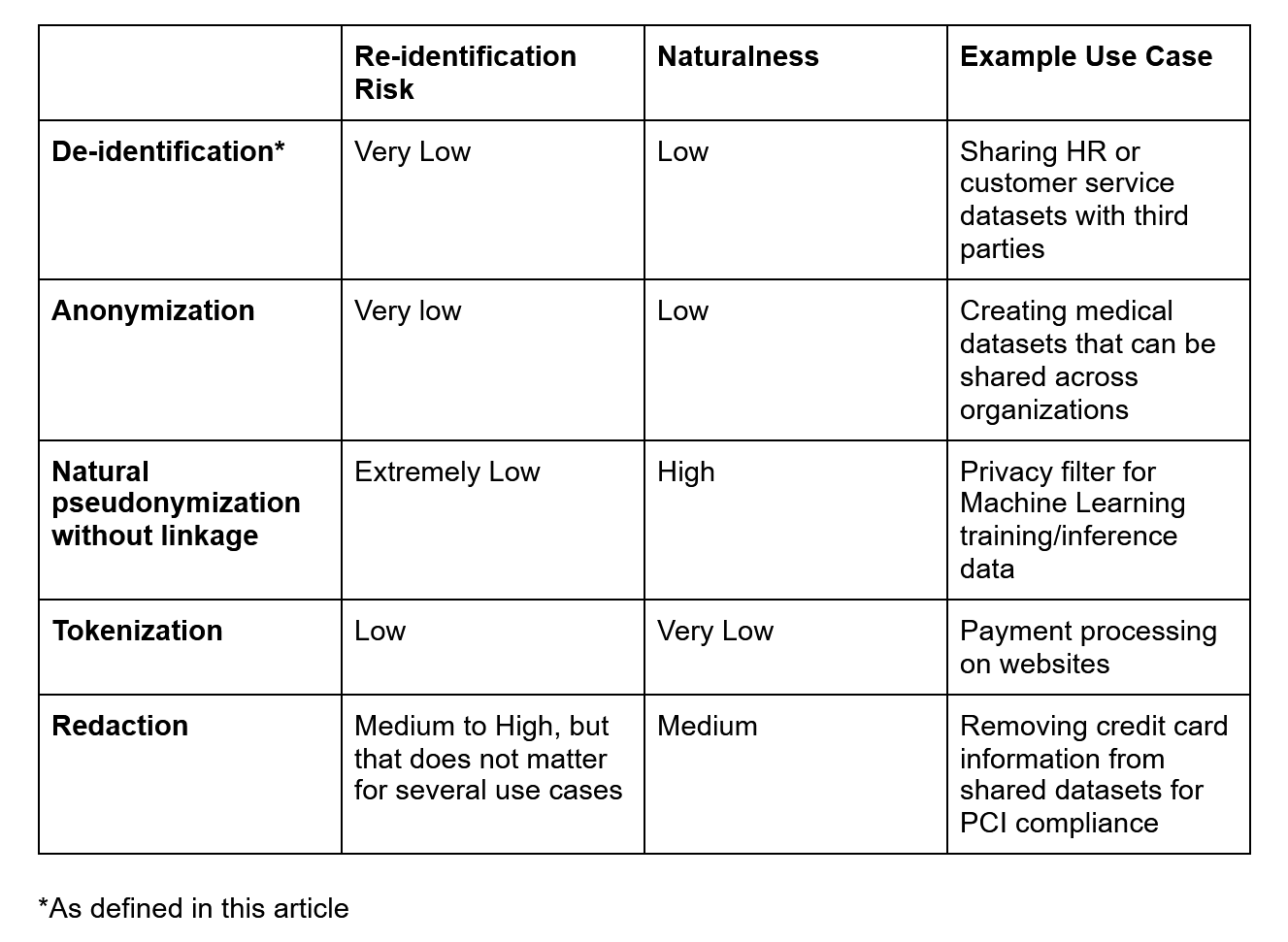
Demystifying De-identification. Understanding key tech for data… | by Patricia Thaine | Towards Data Science
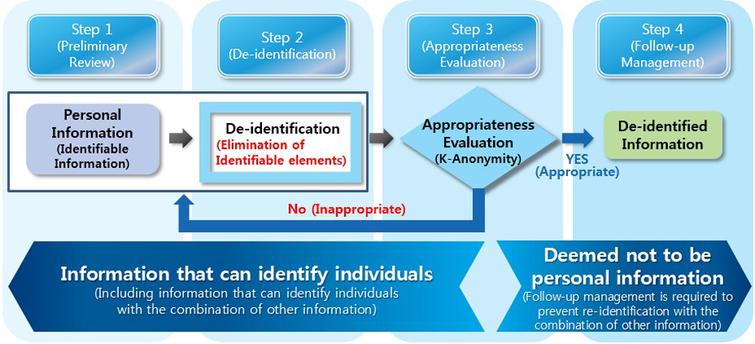
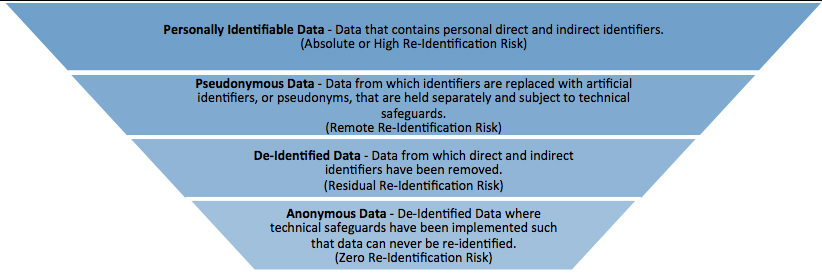
De-identification policy and risk distribution framework for securing personal information - IOS Press

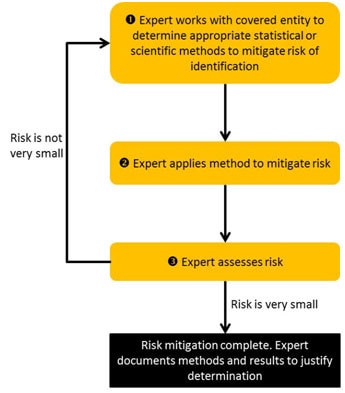
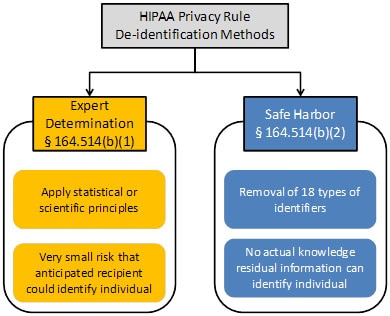
HIPAA De-identification example. Protected Health Identifiers were... | Download Scientific Diagram